
4n6ir.com
Amazon SageMaker Jupyter Notebooks
by John Lukach
Jupyter Notebook end-users only need part of the development environment that AWS Cloud9 or GitHub Codespaces provide. The security operations center (SOC) executes the automation to collect the artifacts to move on quickly, making Amazon SageMaker a good alternative.
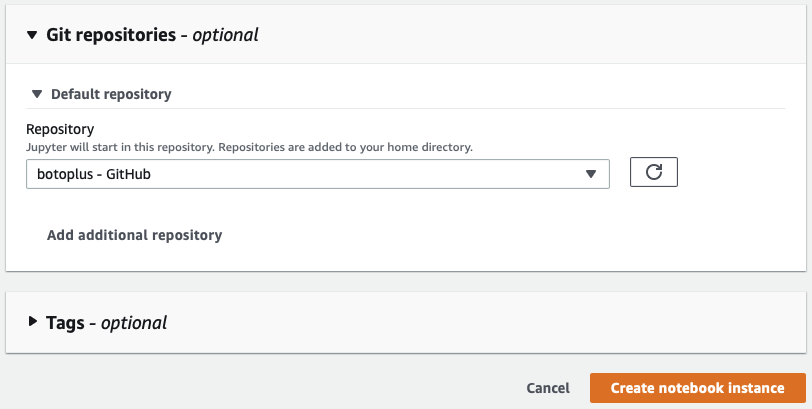
Setup access to the public GitHub repository where the Jupyter Notebooks are maintained. GitHub has a fine-grained personal access token (PAT) option allowing storage in AWS Secrets Manager that supports the least privileged usage of private repositories.
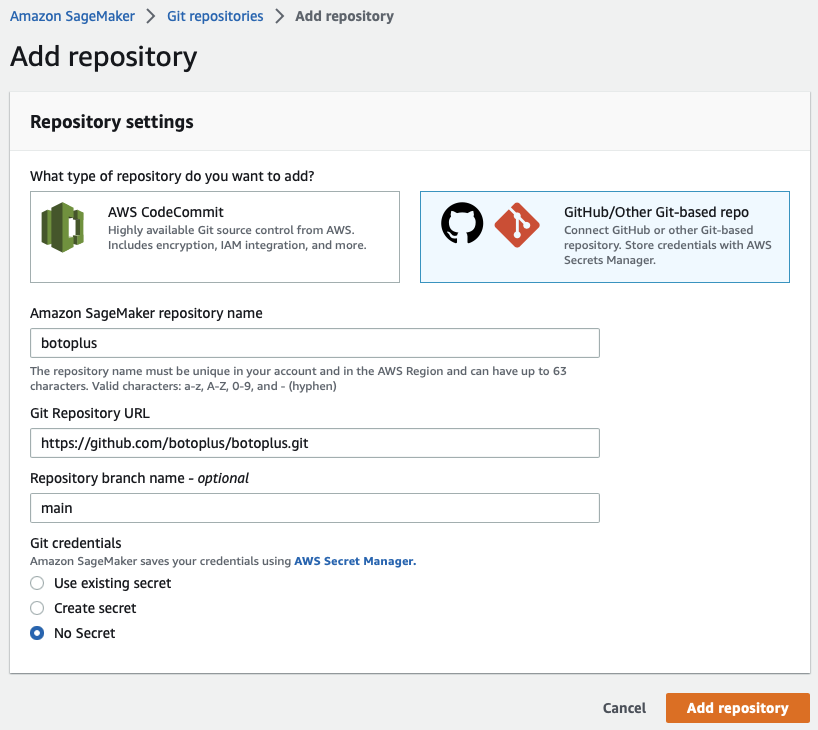
Creating an Identity Access Management (IAM) role will occur while making the first notebook instance. I will use different permissions sets dependent on the resources accessed, but this will minimally get you started just to run Jupyter Notebooks.
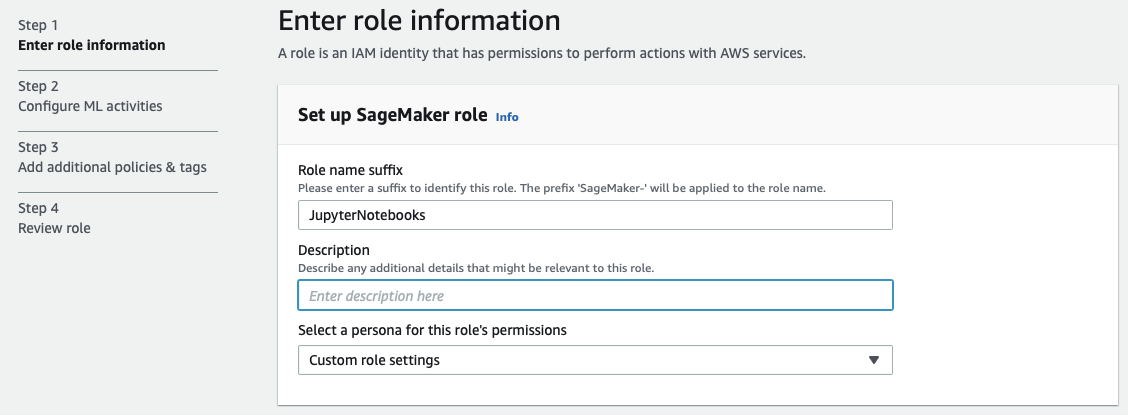
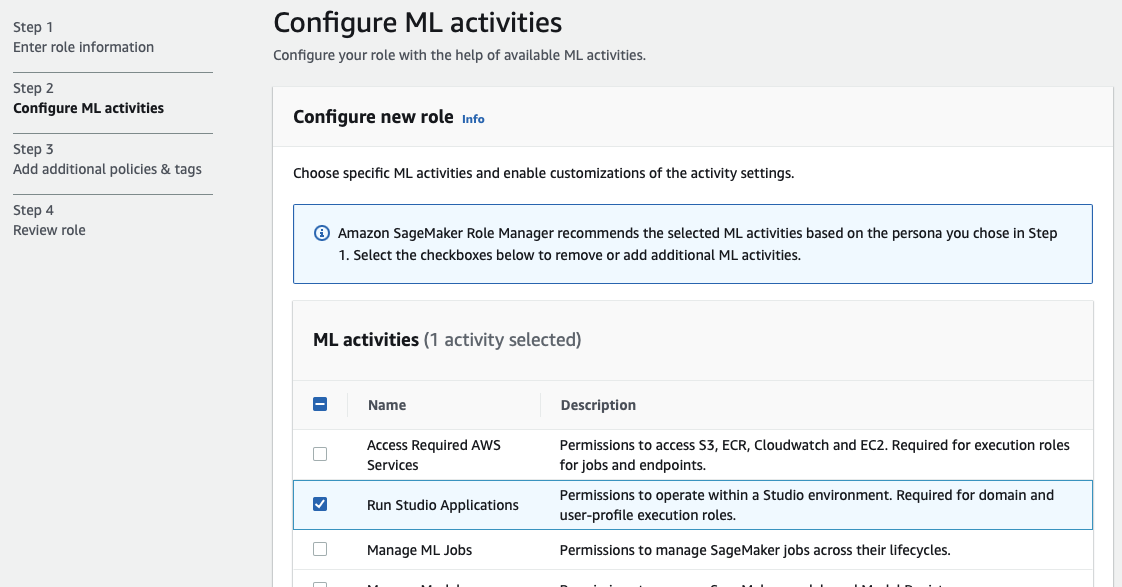
Remember, when creating the notebook instance, the requirements for testing are much different than running in production.
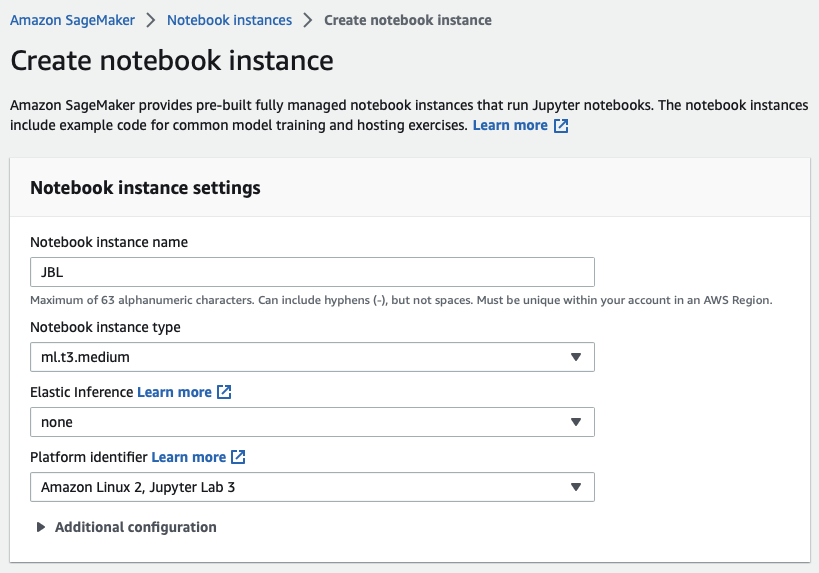
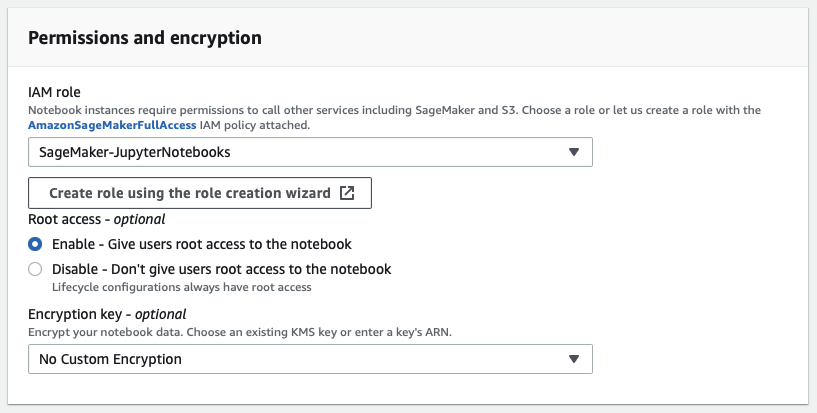
End-users should not have root access, as the lifecycle configuration provides a way to configure the systems without granting this level of permission.
Please attach the notebook instance to a VPC, so it is not on the public Internet, and always use tags.
Watch out for the Jupyter Notebook instances that get left running, as they will not shut off after a period of inactivity hitting the cloud spend.
tags: AWS - Amazon - SageMaker - Jupyter - Notebooks